Bolstering Your Digital Fortress: The Epic Quest for Network Security
Introduction
Step into the exciting realm of network security, where the ongoing struggle to safeguard data and establish digital supremacy unfolds. In the current era of advanced technology, network security isn’t merely a recommended course of action; it is a vital endeavour that every person, company, and governmental entity must embark upon. Embark on this grand journey with us as we explore the significance of network security, its fundamental components, and the astounding strategies that will fortify your digital domain against unwelcome intruders.
The Importance of Network Security
Picture this: your digital kingdom, brimming with invaluable treasures, guarded by fire-breathing dragons – well, not exactly, but you get the idea. Network security is the armour that shields your kingdom, protecting your data, systems, and resources from being pillaged by sneaky cyber pirates. Why is it so vital? Let’s hoist the Jolly Roger and explore:
Data Protection: From personal secrets to corporate treasures, we store sensitive data on our networks. Network security is the guardian that keeps this precious loot from falling into the wrong hands.
Business Continuity: A security breach is like a digital storm – it can disrupt your operations, causing downtime and financial havoc. Network security is your digital umbrella, ensuring business sails smoothly through the storm.
Reputation Management: Nothing tarnishes your digital crown more than a security breach. It can plummet your reputation, leaving you adrift in a sea of mistrust. Invest in robust network security and protect your good name.
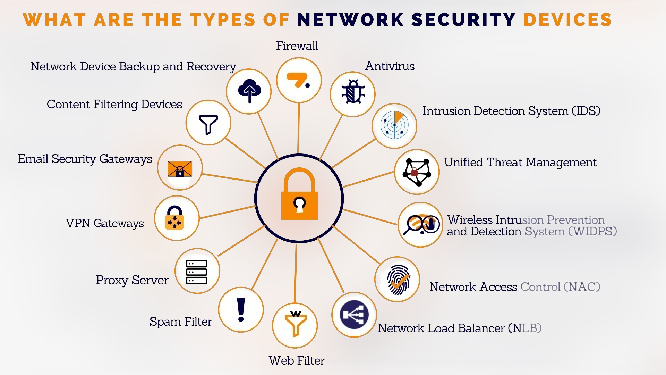
Key Components of Network Security
Now that we’ve set the stage let’s uncover the components that make up the cast of characters in our network security epic:
Firewall: Think of this as the moat around your digital castle – it filters incoming and outgoing traffic, deciding who gets in and who gets kicked out.
Intrusion Detection Systems (IDS) and Intrusion Prevention Systems (IPS): These vigilant sentinels keep watch over your network, detecting troublemakers (IDS) and taking immediate action to stop them (IPS).
Antivirus Software: These are your trusty knights sworn to protect your network from malware, including viruses, worms, and ransomware.
Virtual Private Network (VPN): Your network’s secret passage – it encrypts your traffic, ensuring secure communication, even in the wilds of the internet.
Access Control: The gatekeepers of your network – they decide who gets the keys to the kingdom and who stays out in the cold.
Regular Updates and Patch Management: Think of this as the ongoing training of your digital army. Keep your software and security systems up-to-date to tackle vulnerabilities head-on.
Data Encryption: Your language of secrets – it turns sensitive data into unreadable code, even if someone manages to sneak a peek.
Best Practices for Network Security
The epic doesn’t end with assembling your cast; there’s an ongoing adventure to undertake. Here are some best practices to ensure your network security remains legendary:
Employee Training: Equip your troops (employees) with knowledge and the right tools for safe online adventures.
Regular Audits and Testing: Like sharpening your swords and reinforcing your walls – keep your defences tip-top by regularly auditing and testing your network security.
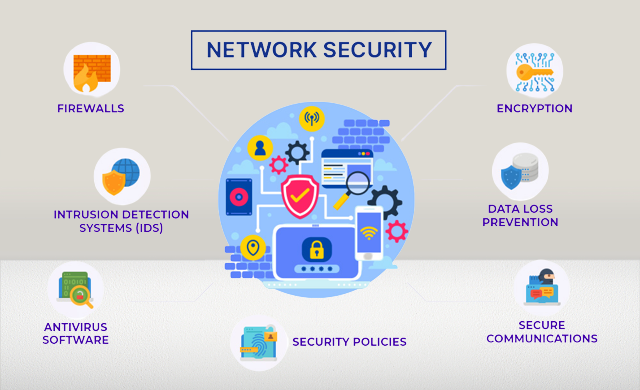
Strong Password Policies: Passwords are your digital keys – make them strong and unbreakable.
Network Segmentation: Divide and conquer – isolate sensitive data to limit the impact of any potential breaches.
Incident Response Plan: Every hero needs a plan – create a battle strategy for responding to security incidents.
Security Updates: Stay alert to the latest threats and update your defences accordingly. Information is your best weapon.
Conclusion
In the electrifying world of network security, vigilance is your greatest ally. Protecting your digital kingdom isn’t a one-time quest; it’s a never-ending saga. By investing in robust network security and following these best practices, you’ll emerge as the legendary protector of your data, systems, and reputation in the ever-changing landscape of cyber threats. Arm yourself, stay vigilant, and let the epic adventure of network security begin!
FAQs
What’s the buzz about network security, and why should I care?
Network security is like the guardian of your digital kingdom, protecting your precious data, fortifying your defences, and ensuring your realm remains untarnished. It’s essential because it safeguards your treasures, keeps the peace, and helps you stay on the right side of the law.
Tell me more about the key players in network security. What are the main characters in this epic saga?
In the grand tapestry of network security, we have our heroes:
Firewalls, the gatekeepers
IDS and IPS, the vigilant protectors
Antivirus software, the virus-slaying champions
VPNs, the secret keepers
Access control, the bouncers
Updates and patches, the ever-evolving army
Data encryption, the master of disguise
How do these firewalls work, and why are they the first line of defence in network security?
Picture firewalls as the formidable moats around your digital castle. They’re like the wise old gatekeepers, allowing or denying access to your kingdom. In other words, they’re your initial defence against malicious invaders.
What’s the dynamic duo of IDS and IPS, and why should I care about them?
IDS and IPS are your trusty sidekicks. IDS monitors your network for trouble, while IPS jumps into action when danger is afoot. They’re the dynamic duo that helps you spot and thwart potential threats.
Why does my network need antivirus software, and how does it save the day?
Antivirus software is like the superhero squad protecting your digital turf. They sniff out and eliminate malware villains, such as viruses and ransomware, that could wreak havoc and steal your data.
How does a VPN add an extra layer of excitement to network security?
A VPN is like a secret passage that leads to hidden treasures. It encrypts your data, creating a secure tunnel for your information to travel through, ensuring your secrets stay safe.
What’s the playbook for top-notch network security? What are the epic quests and legendary battles to be fought?
The playbook includes:
Training your troops (employees).
Conducting regular security audits.
Arming them with strong passwords.
Dividing and conquering with network segmentation.
Creating a battle plan for responding to security incidents.
Stay informed and keep your defences sharp to face the challenges.
Why is employee training a crucial part of network security?
Training your troops is like giving them the map to navigate the digital jungle. Educating your employees about potential risks and best practices is vital to avoid security breaches caused by innocent mistakes.
What’s the battle plan when my network security is compromised?
In the heat of battle, follow your incident response plan. Isolate the affected areas, launch a full-scale investigation, contain the breach, and start the remediation process. Remember to inform the relevant authorities and your allies if needed.
Is network security a one-time quest or an ongoing adventure?
Network security is an ever-evolving adventure. Cyber threats are like shape-shifters, constantly changing. To keep your kingdom safe, you must remain vigilant, adapt to the shifting landscape, and continuously upgrade your defences.
Related Article:
Risk Assessment and Management: Paving the Path to Success



