Safeguarding Data: The Thrilling Trio of Information Security
Introduction
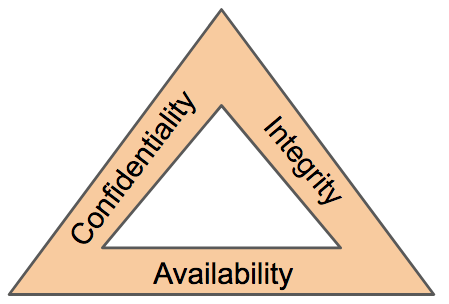
In today’s high-tech world, information is pure gold. It’s the digital treasure that individuals, businesses, and governments can’t afford to lose. That’s where our heroes, the Confidentiality, Integrity, and Availability (CIA) triad, come to the rescue. They’re like the guardians of the data realm, ensuring it stays safe and sound. In this article, we’ll go on an adventure to discover the superpowers of the CIA triad and how they’re here to save the day in the world of information security.
Confidentiality: The Keeper of Secrets
Confidentiality, the first member of our trio, is the data’s best-kept secret. It’s like a bouncer at the exclusive club of sensitive information. Its job? To make sure that only the right people get access. Think of it as the security guard for your info, trade secrets, and classified government files. With tricks like encryption, access controls, and user authentication, it keeps the nosy villains at bay, protecting our most valuable secrets.
Integrity: The Truth Serum
Data integrity is the hero we need to keep information honest. Imagine your data as a truth-telling superhero. It ensures that your data doesn’t get messed with, corrupted, or altered in any way. It’s like the guardian of trustworthiness, providing the information is always accurate. It uses techniques like digital signatures, checksums, and hash functions to maintain data integrity. Without it, you’d be dealing with misinformation, fraud, or chaos!

Availability: Always-On Avenger
Our third hero, Availability, is all about keeping the data accessible and ready for action. It’s like the lifeline that ensures you can reach your data whenever needed. Availability is your best friend when your business relies on uninterrupted services, or national security depends on timely information access. It uses tools like backup systems, redundancy, fault tolerance, and disaster recovery plans to make sure the data is always there, even in the face of adversity
The Dynamic Trio in Action
These three champions of the CIA triad work together in a dynamic dance to protect your data. A breach in one area can trigger a domino effect, putting the entire information security ecosystem at risk. For example, if the confidentiality shield is compromised, it can lead to unauthorized changes (messing with integrity) or a complete lockdown (affecting Availability). It’s like a tightly woven safety net, ensuring data remains secure, reliable, and accessible.
In the Real World
The CIA triad isn’t just a concept – it’s the superhero team actively saving the day in the real world. Here are some everyday examples:
Healthcare:
Think of medical records that contain your most personal information. They’re kept under lock and key (confidentiality) to protect your privacy. Data integrity ensures that your medical history remains accurate, while Availability is crucial for healthcare professionals to access critical information in emergencies.
Government and Defense:
Government agencies handle classified info that’s top-secret (confidentiality), and the integrity of this data is a matter of national security. Availability is also vital for communication and intelligence systems to ensure effective decision-making and emergency response.
Conclusion
The Confidentiality, Integrity, and Availability (CIA) triad is not just a dry concept; it’s the superhero team that’s on a mission to keep your data safe, sound, and always ready for action. By mastering the secrets of this trio, organizations and individuals can be the guardians of their digital assets, ensuring their information is secure, truthful, and ready at a moment’s notice. Balancing these three superheroes is the key to protecting your data and earning the trust of everyone in our increasingly connected, data-driven world.
FAQs
What’s the Deal with the CIA Triad?
The CIA Triad is like the Avengers of information security. It comprises Confidentiality, Integrity, and Availability – the three powerhouses that keep our digital world safe and sound.
Tell Me More About Confidentiality. What’s It All About?
Confidentiality is the guardian of secrets. It’s like the trusty gatekeeper that decides who gets to enter the exclusive club of sensitive data. Its mission is to keep unauthorized intruders at bay and protect your most precious secrets.
How Does Data Integrity Save the Day?
Data Integrity is the superhero of accuracy. It ensures that your data doesn’t get tampered with or corrupted. It’s like the truth serum for your information, keeping it reliable and trustworthy.
What’s Availability’s Role in All This?
Availability is the always-on Avenger. It’s the lifeline that guarantees your data is there whenever you need it. Whether it’s for business operations or national security, Availability makes sure your data is ready for action 24/7.
How Do These Three Components Play Together?
They’re like a well-coordinated team. A breach in one area can trigger a chain reaction affecting others. They work together to create an impenetrable shield for your data.
Give Me Real-World Examples of the CIA Triad in Action.
Sure thing! Think of healthcare, where patient records are kept confidential, and data integrity ensures accuracy. E-commerce platforms rely on confidentiality for customer data, transaction integrity, and Availability for 24/7 shopping.
Can I Customize the CIA Triad to Fit My Needs?
Absolutely! You can adjust the CIA Triad to match your specific needs. Depending on your goals, you can prioritize confidentiality, integrity, or availability.
How Can I Put the CIA Triad into Practice?
Implementing the CIA Triad involves various technical measures, policies, and procedures. Encryption, access controls, user authentication, backup systems, and more are part of the toolkit.
What Happens If I Neglect the CIA Triad?
Neglecting the CIA Triad can lead to data breaches, loss, unauthorized access, and corruption. It’s like leaving the front door open for digital intruders, and the consequences can be disastrous.
Related Article:
Safeguarding Your Digital World: The ABCs of Information Security



